Platform Security¶
Overview¶
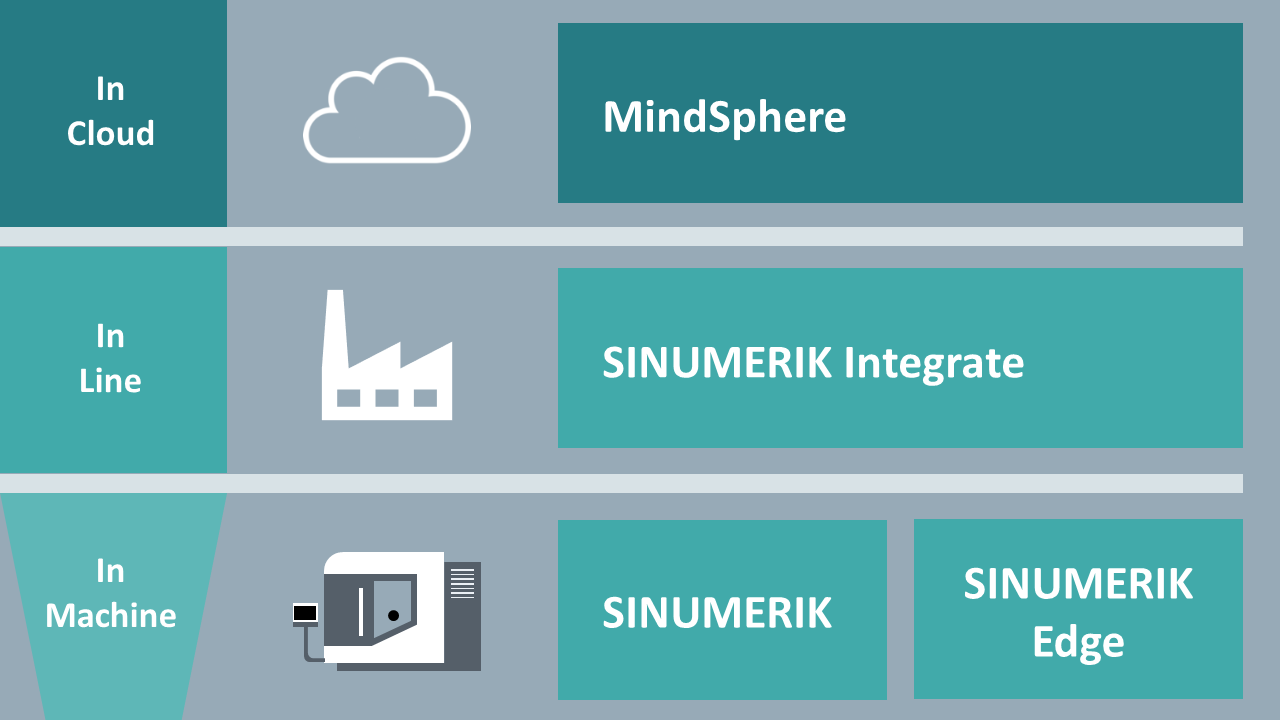
SINUMERIK Edge is a remote-controlled Edge-Device, which can be used within an extended IoT/OT architecture both as field gateway and computation node for any user workloads. The SINUMERIK Edge thus enables vertical information and data processing flow between all layers:
-
In Machine
-
In Line
-
In Cloud
Digitalization layers:
This also includes the temporary or permanent storage of process data. Thus, SINUMERIK Edge is responsible for ensuring that its security architecture does not allow any regression/regression of the data erosion of the existing network security and data protection level. To the individual security mechanisms of SINUMERIK Edge, it is necessary to organizational support here as well.
SINUMERIK Edge is a standard IPC with a special operating system that forms together with Insights Hub the SINUMERIK Edge Ecosystem. The SINUMERIK Edge offers high-frequency data access to internal control data, additional computing power at the machine, update capability through the connection to Insights Hub – finally a secure platform for applications that generate added value based on the data.
The SINUMERIK Edge is a product of its own. The SINUMERIK Edge apps that can be executed are separate products with corresponding order numbers.
With the App-SDK package the customer can develop his own apps (e.g. Eclipse as development environment). To publish the created apps and deploy them on SINUMERIK Edge devices, Manage MySINUMERIK Edge /App Management is required.
The SINUMERIK Edge works in the daily operations without Insights Hub. However, the commissioning and the installation/configuration of firmware and SINUMERIK Edge apps requires the connection to Insights Hub.
Connection and wiring of SINUMERIK Edge:
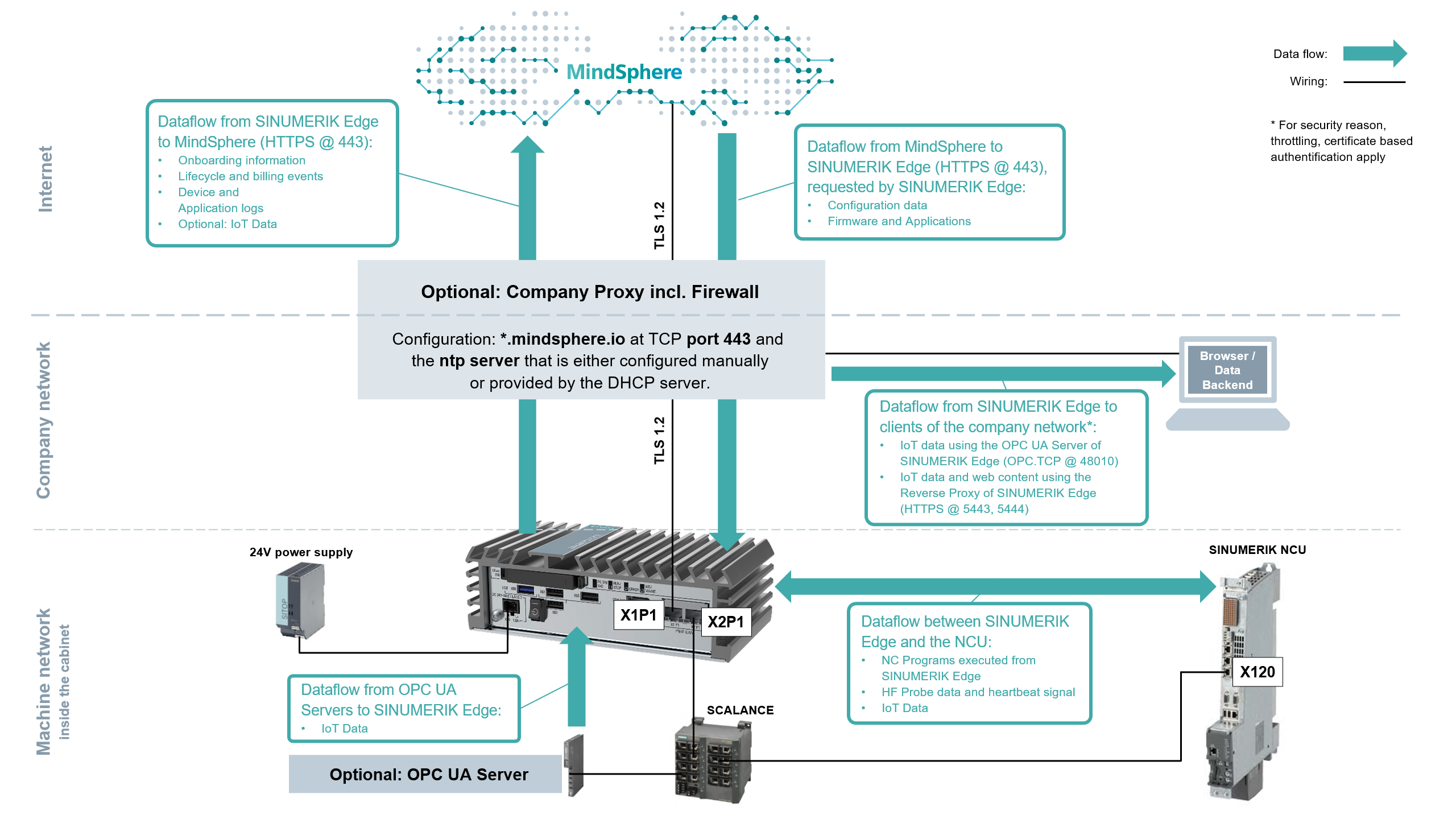
The SINUMERIK Edge is equipped with 2 physical network connections (RJ45), which, according to the manual, are to be used for the connection to the In Machine and In Line Level.
Make sure that the port assignment is correct for the following reasons:
-
For the "In Machine" network, a mainly unprotected communication is assumed
-
For the "In Machine" network, an uncontrolled connectivity to higher networks (In Line, In Cloud) is not possible.
The SINUMERIK Edge guarantees the isolation of the network through a multi-level network architecture of both networks, which is only overcome by an application-defined data flow. Using container technology, further mechanisms exist for Isolation of the workload (edge application) in terms of network, memory and CPU resources.
The communication of the SINUMERIK Edge in the direction of "In Cloud" and "In Line" is always established via an encrypted end-to-end channel (TLS 1.2). In addition, the integration a PKI-based trust chain is supported. Thus, both a restriction to only allowed communication partners as well as the trustworthy transmission is ensured. For the in-line data exchange in environments with special security requirements a client-based authorization via client certificates is possible in addition.
The initial exchange of the required certificates for secure communication between Edge Management System (In Cloud) and SINUMERIK Edge (In Machine) is implemented during the so-called onboarding process. The onboarding process includes the exchange of a "shared secret" that connects a logical device (Insights Hub Asset) with a physical device (SINUMERIK Edge). Since this exchange does not happen via the same communication infrastructure, compromising may occur during the onboarding. A second aspect of onboarding is the linking / integration of Insights Hub IoT Services (Timeseries Store, File Store, Monitor, ...) in the correct Insights Hub Tenants. The SINUMERIK Edge-Platform also ensures that a data flow into a tenant or asset not designated for this purpose can be established at no point.
Note
The basis for this is an existing Insights Hub Subscription (at least an IoT Value Plan S).
The SINUMERIK Edge communicates solely through outgoing connections. This means that no exposition of the SINUMERIK Edge is needed on In Line or In Cloud Level. This scenario is not recommended.
Regardless of this configuration, the access to the Insights Hub endpoints from the SINUMERIK Edge must be guaranteed temporarily. This concerns the onboarding, the firmware update or the (de)-installation of edge applications. The SINUMERIK Edge not only enables applications (Industrial App) to provide data via a controlled way In Cloud, rather these applications can provide user interfaces and/or interfaces (APIs) to create new workflows (in line) or to supplement existing ones. For this purpose, applications may provide their own user and access management capabilities. The corresponding security notes can be found in the respective documentation.
The communication of the SINUMERIK Edge with the SINUMERIK takes place only via the "In Machine" network and is encrypted according to the respective protocols. However, the authorization mechanisms vary depending on the protocol used. Since some protocols are secured with weak protection mechanisms, it is important in these cases to adhere to adequate password guidelines and to ensure organizationally that passwords are never or only in urgent cases stored.
In order to maintain a high security level of the SINUMERIK Edge over a long period of time the firmware is continuously developed and hardened, based on multiple vulnerability checks, virus scans as well as penetration tests that had been performed for the SINUMERIK Edge software. This is necessary in order to adapt to the increasing cyber security threat situation. As part of the SINUMERIK Edge firmware, an update mechanism is available for this purpose, which is integrated into the corresponding IT process as part of a continuous security strategy.
The SINUMERIK Edge does not provide an onboard virus scanner as part of the firmware. The customer needs to run virus scans for SINUMERIK Edge before uploading their applications to the Insights Hub.
The in- and outbound communication is protected by a firewall that is configured and activated as part of the SINUMERIK Edge firmware. Not needed firewall rules had been removed. The interfaces cannot be accessed directly from a SINUMERIK Edge application without using the predefined adapter functions of the App-SDK.
Users with IP based filtering on their firewall can use the following two static IPs for whitelisting the data upload traffic:
- 75.2.111.226
- 99.83.250.213
A strong password policy forces the customer to change the password of the default user of SINUMERIK Edge’s firmware (linux console) and the Miniweb at first login. This is described in the system manual.
By default, edge user that is used for Linux console login will have it's password expiration date set to 90 days.
If desired, users can change the default password expiration duration by issuing below command. Passing the number -1 as number of days will remove expiration duration indefinitely. Allowed values for number of days are -1, 30, 90, 180 and 360.
sudo chage --maxdays <number-of-days> edge
In addition, the SINUMERIK Edge is protected against undesired manipulation or weakening of the security features on both firmware and application level as follows:
SINUMERIK Edge Security Features¶
SINUMERIK Edge follows security guidance from international standards such as IEC 62443-4-2 Security for Industrial Automation and Control Systems Part 4-2: Technical Security Requirements for IACS Components.
Data protection in general¶
Protects the manufacturing process through application-specific access control.
Protects industrial business by focusing on longterm stability and avoidance of incompatible changes (if possible).
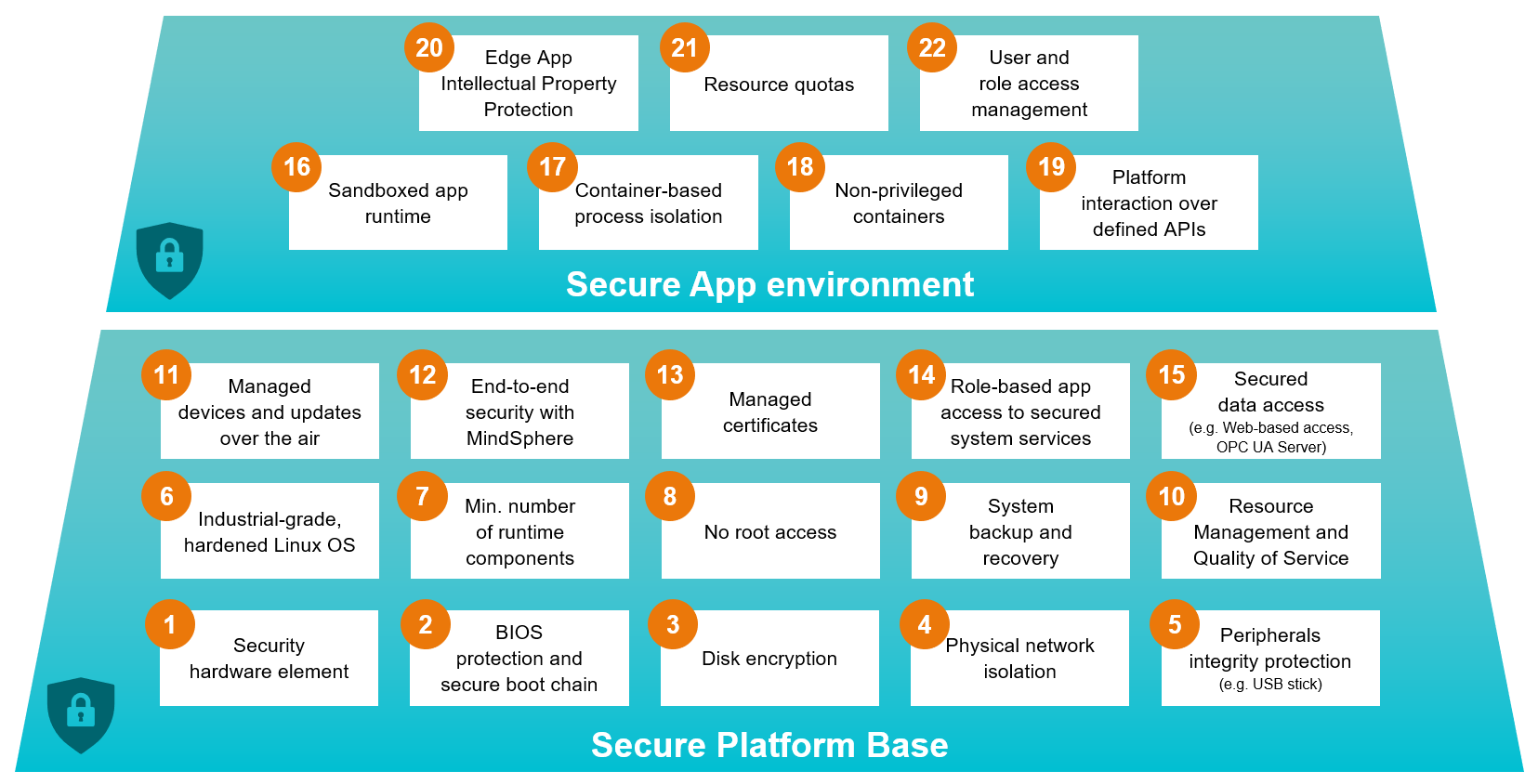
1. Security Hardware Element¶
Security Hardware Element is a chip, that has an initial secret for the secure boot chain to build on and disk encryption.
2. BIOS protection and secure boot chain¶
BIOS protection is based on a password, to avoid changes; secure boot chain: only the SINUMERIK Edge operating system or service stick may boot.
3. Disk encryption¶
The data is decrypted only on the device where the hard drive is built in (device decrypts data upon booting process). The encryption is based on a secret, which can only be decrypted on that device.
4. Physical network isolation¶
There are two interfaces: X1 P1 to external network and X2 P1 to machine network. Those interfaces cannot be bridged. That makes it impossible for externals to attack the machine tool controller through the Edge data access and allows processing only by certified apps and through security layers.
5. Peripherals integrity protection¶
Only keypad, mouse and known devices (onboarding stick; service USB stick, etc.) are supported. Other devices are ignored.
6. Industrial-grade, hardened Linux OS¶
Linux operating system, which is hardened by our security standards, e.g. internal communication via protected virtual network layers.
7. Minimum number of runtime components¶
The operating system is designed in an efficient manner, which means only necessary, specially tailored components are used, which minimizes the possibilities for externals to attack the device.
8. No root access¶
There is no root user access to the system. A standard user only has limited access, so that side-loading of apps/viruses is not possible.
9. System backup and recovery¶
A system backup and recovery can only be done by a service stick, so that e.g. any backup from unprotected systems are avoided.
10. Resource management and quality of service¶
There is a limitation of resource usage for apps, so that the system components always have enough processing power to operate. This eliminates the risk of denial of service attacks.
11. Managed devices and updates over the air¶
Applications strictly need to be deployed on devices via cloud. That ensures integrity and availability according to SINUMERIK Edge security paradigm/ concept.
12. End-to-end security with Insights Hub Edge Management¶
TLS 1.2 is used for the connection between the device and Insights Hub, which prevents the spying of production relevant data and protects the intellectual property of the machine user.
13. Managed certificates¶
Miniweb creates a certificate, that can be imported to the client browser to secure the communication between browser and Edge. In that way a secure end-to-end connection is established.
14. Role-based app access to secured system services¶
Only authorized apps may access certain services to ensure security.
15. Secured data access¶
Access to App UIs is established via SINUMERIK Edge Miniweb (HTPPS connection via Port 5443). Miniweb then roots further to the App, which results in a single control point for outbound communication.
16. Sandboxed app runtime¶
An isolated container-based environment is used, which ensures that apps do not disturb each other nor the system. The run in dedicated isolated environments with defined interfaces to the system.
17. Container-based process isolation¶
Apps are isolated from each other. A prioritization and scheduling of processes is done by the platform, which results in enhanced stability and reliability of the system.
18. Non-privileged containers¶
Containers may never directly access the Linux kernel, only via interfaces (described in Developer Documentation). That results in enhanced stability of the system.
19. Platform interaction over defined APIs¶
Access to system services/ interfaces and internal communication only is established via software interfaces delivered by the App-SDK. In this way, our interfaces for external communication are being addressed, too.
20. Edge App intellectual property protection¶
The app container uploaded to Insights Hub is encrypted.
21. Resource quotas¶
Every container gets its own quota (resources), which result in enhanced stability and reliability of the system.
22. User and role access management¶
Roles, users and login can be configured via Miniweb, which prevents unauthorized externals accessing Edge application data.
Further security features¶
SINUMERIK Adapter protects the manufacturers‘ intellectual property by removing sensitive content in HF Probe data.
SINUMERIK Edge Security Disclaimer¶
Siemens provides products and solutions with industrial security functions that support the secure operation of plants, systems, machines and networks.
In order to protect plants, systems, machines and networks against cyber threats, it is necessary to implement – and continuously maintain – a holistic, state-of-the-art industrial security concept. Siemens’ products and solutions constitute one element of such a concept.
Customers are responsible for preventing unauthorized access to their plants, systems, machines and networks. Such systems, machines and components should only be connected to an enterprise network or the internet if and to the extent such a connection is necessary and only when appropriate security measures (e.g. firewalls and/or network segmentation) are in place.
For additional information on industrial security measures that may be implemented, please visit https://www.siemens.com/industrialsecurity.
Siemens’ products and solutions undergo continuous development to make them more secure. Siemens strongly recommends that product updates are applied as soon as they are available and that the latest product versions are used. Use of product versions that are no longer supported, and failure to apply the latest updates may increase customer’s exposure to cyber threats.
To stay informed about product updates, subscribe to the Siemens Industrial Security RSS Feed under https://www.siemens.com/industrialsecurity.
Data transfer and storage¶
Transfer of exported data files have to been secured by technical means like encrypted emails and USB-Sticks, etc., especially in the public internet. Exported data files have to be stored access restricted within the production area (e.g. access restriction to sharepoints, data bases, etc. by user management with credentials)
Multi-factor authentication on Insights Hub¶
You can further increase security by activating multi-factor authentication (MFA). Activating MFA is therefore recommended for your tenant. MFA adds another layer of authentication to standard to authentication by adding a user name and password. Multi-factor authentication is not a standard Insights Hub setting. Contact Insights Hub for activation.
Any questions left?
Except where otherwise noted, content on this site is licensed under the The Siemens Inner Source License - 1.1.