Obtaining Auto-Generated Agent Certificate¶
To connect with the Insights Hub environment, MQTT agents need to authenticate themselves with a unique X.509 certificate and key pair. These can be simply downloaded from the Asset Manager or alternatively using the MindConnect MQTT API auto-generated certificate and key pair can be downloaded.
Obtaining auto-generated agent certificate from API¶
Prerequisites¶
-
Insights Hub environment: Within this document, the parameter
<tenantId>is the name of your Insights Hub environment. -
Gawk: Certificate content as JSON string, you need to escape newline characters in your certificate file. You can print the escaped version.
Info
Auto-Generated Agent Certificate is currently available in region Europe 1.
You need to make a POST request to agentCertificates with the following JSON payload:
Info
The <TOKEN> header parameter needs to be replaced by an actual token.
The name payload parameter needs to be replaced by an actual name. This field is mandatory.
The owner payload parameter may be replaced by an owner. This field is optional.
Sample HTTP request body:
POST /api/mindconnectmqtt/v3/agentCertificates HTTP/1.1
Host: gateway.eu1.mindsphere.io
Content-Type: application/json
Authorization: Bearer <TOKEN>
{
"name": "device001",
"owner": "somebody@some.com"
}
Sample response body:
{
"id": "01G16QJSRNKA3JD4DQE2Z7KPEK",
"name": "device001",
"agentName": "mqtt1_device001",
"owner": "somebody@some.com",
"agentId": "9eyf37799b5949099a5287a547f8e001",
"clientId": "mqtt1_device001",
"privateKey": "-----BEGIN RSA PRIVATE KEY-----\nMIIEAkpNm5P/3hHGKJ+ swJe9A==\n-----END RSA PRIVATE KEY-----\n",
"publicKey": "-----BEGIN CERTIFICATE-----\nMIIDWTCCAk\n-----END CERTIFICATE-----\n",
"status": "READY"
}
Storing private key and public key in separate files¶
The generated private key and public key are confidential. You must securely store it.
Contents of the privateKey and publicKey must be escaped in order to use it in the JSON payload then they need to be stored in separate files. You can use the awk command:
LINUX / WINDOWS:
awk '{gsub(/\\n/,"\n")}1' public-key.pem > public-key.txt && mv public-key.txt public-key.pem
awk '{gsub(/\\n/,"\n")}1' private-key.key > private-key.txt && mv private-key.txt private-key.key
Sample output:
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAt0RP2Fxxt2GUJAkpNm5P/3hHGKJ+9opB0zNnEZqp/14VYfKO
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
B3+jq7aqs2VIqV06Xlw7Wxs2nZ76Vrerz2DXbPc7sbCKLKFVMPcbeiQJ/hNnFMSL
OuBGKqsu2vXgDjlgUm8Z+DxVk4/swkYdnjq180vtjJMhiUpBctJe9A==
-----END RSA PRIVATE KEY-----
Obtaining auto-generated agent certificate from UI¶
- Login to your environment.
!!! note The MindConnect MQTT API Services are currently available in regions EU1.
**2.**Launch the "Asset Manager" application from the Launchpad.
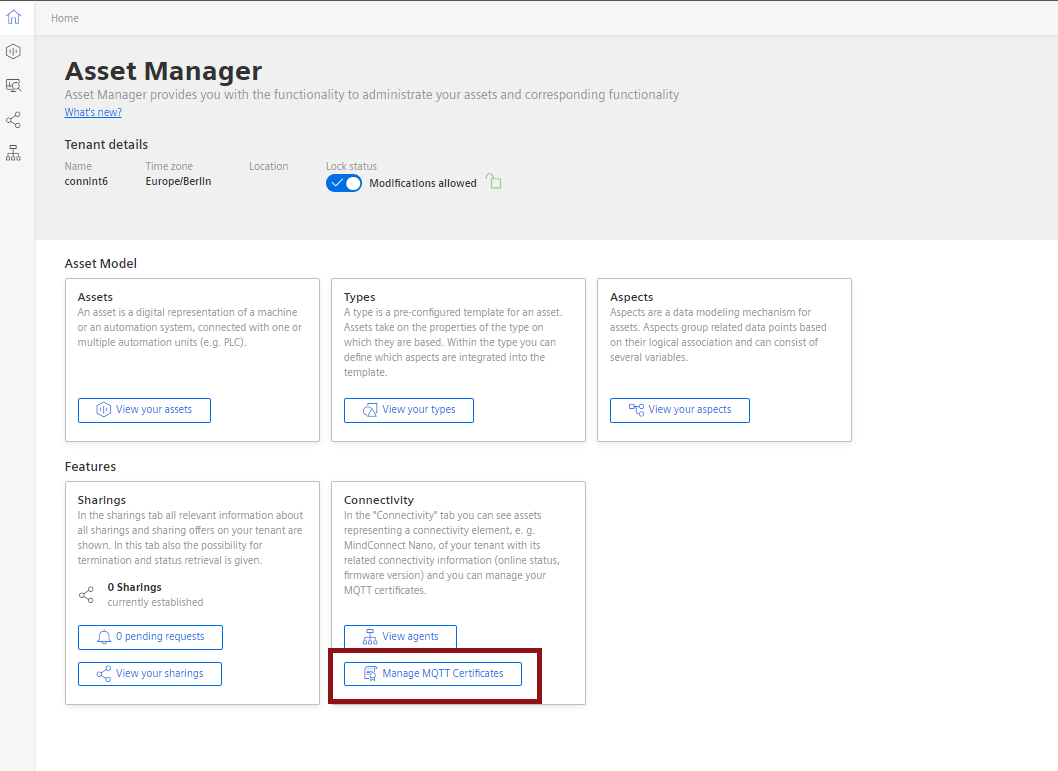
**3.**Go to "Manage MQTT Certificates" under "Connectivity".
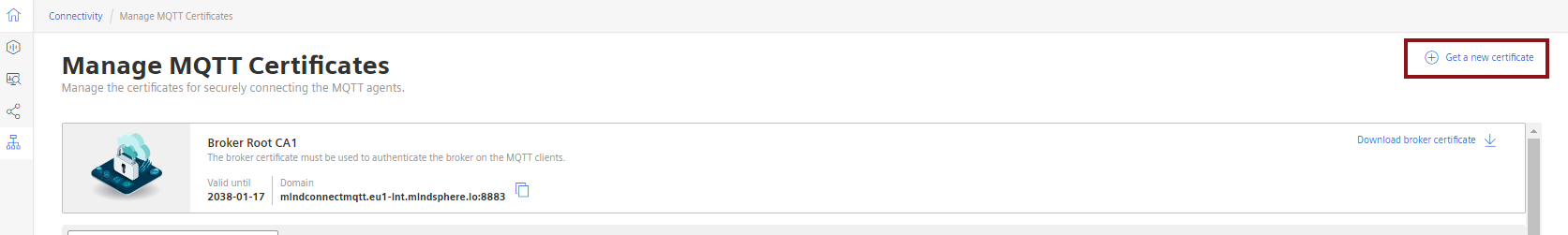
**4.**Go to "Get a new certificate" under "Manage MQTT Certificates".
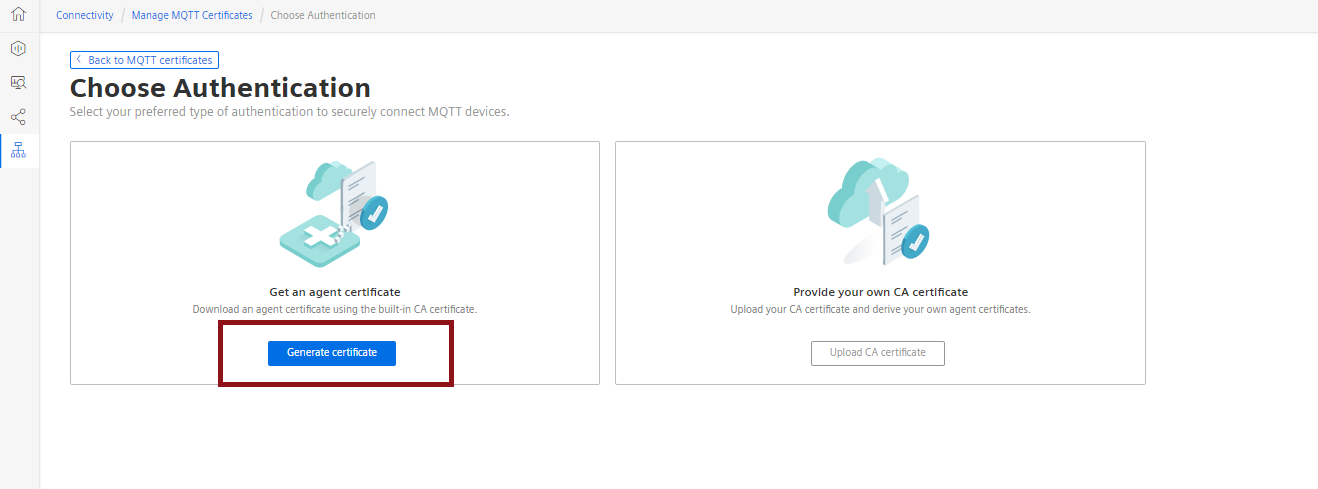
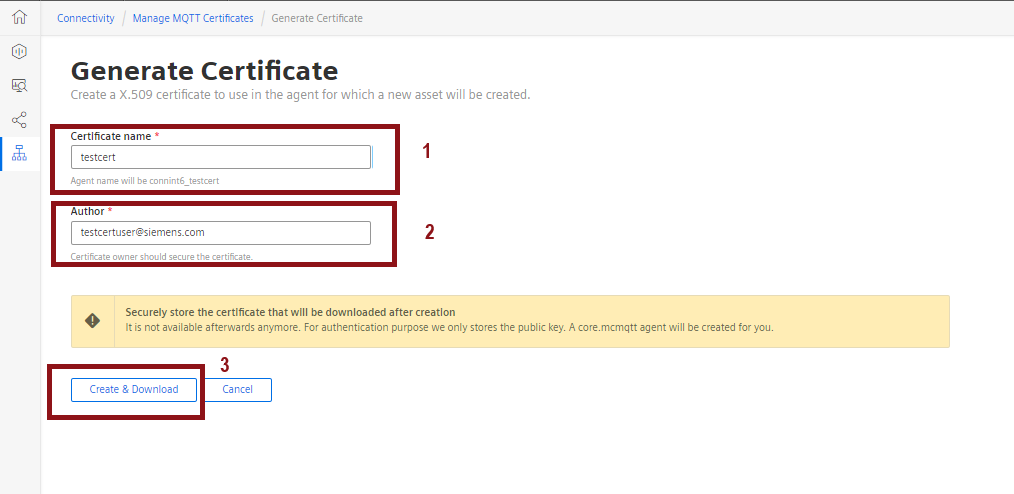
**5.**Choose authentication type as get an agent certificate and click "Generate Certificate".
**6.**Provide a name and author for your certificate then click "Create & Download". After this step key and pem files will be downloaded automatically in your device.
Agent Connection¶
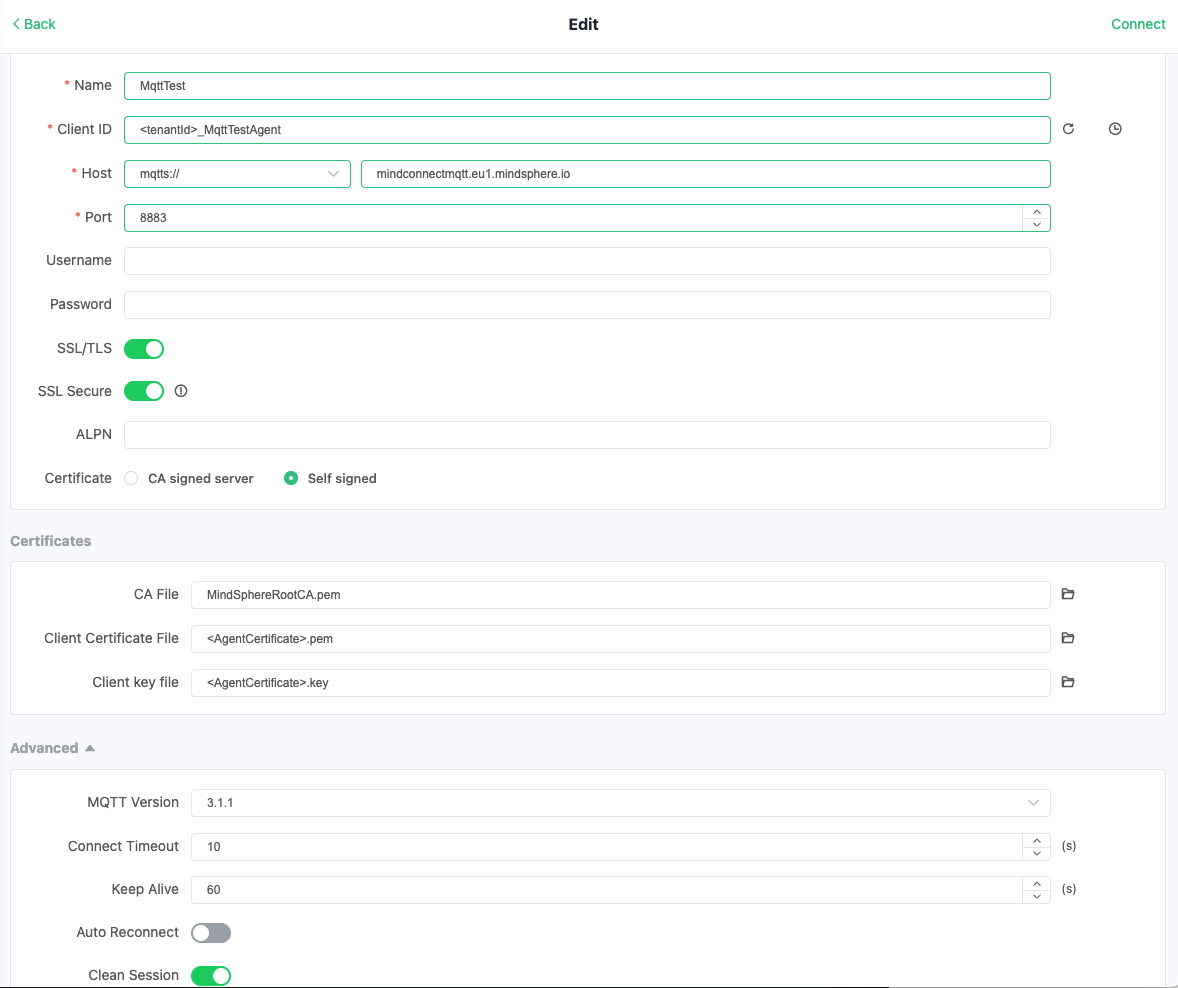
MQTTX Connection Example¶
Except where otherwise noted, content on this site is licensed under the Development License Agreement.