MindConnect General Security Principles¶
The following are the security principles of MindConnect services:
- Communication between devices and Industrial IoT cloud services through HTTPS and signed URLs.
- Authentication and authorization using OAuth 2.0 mechanisms.
- Security tokens have a limited time span of validity and must be renewed.
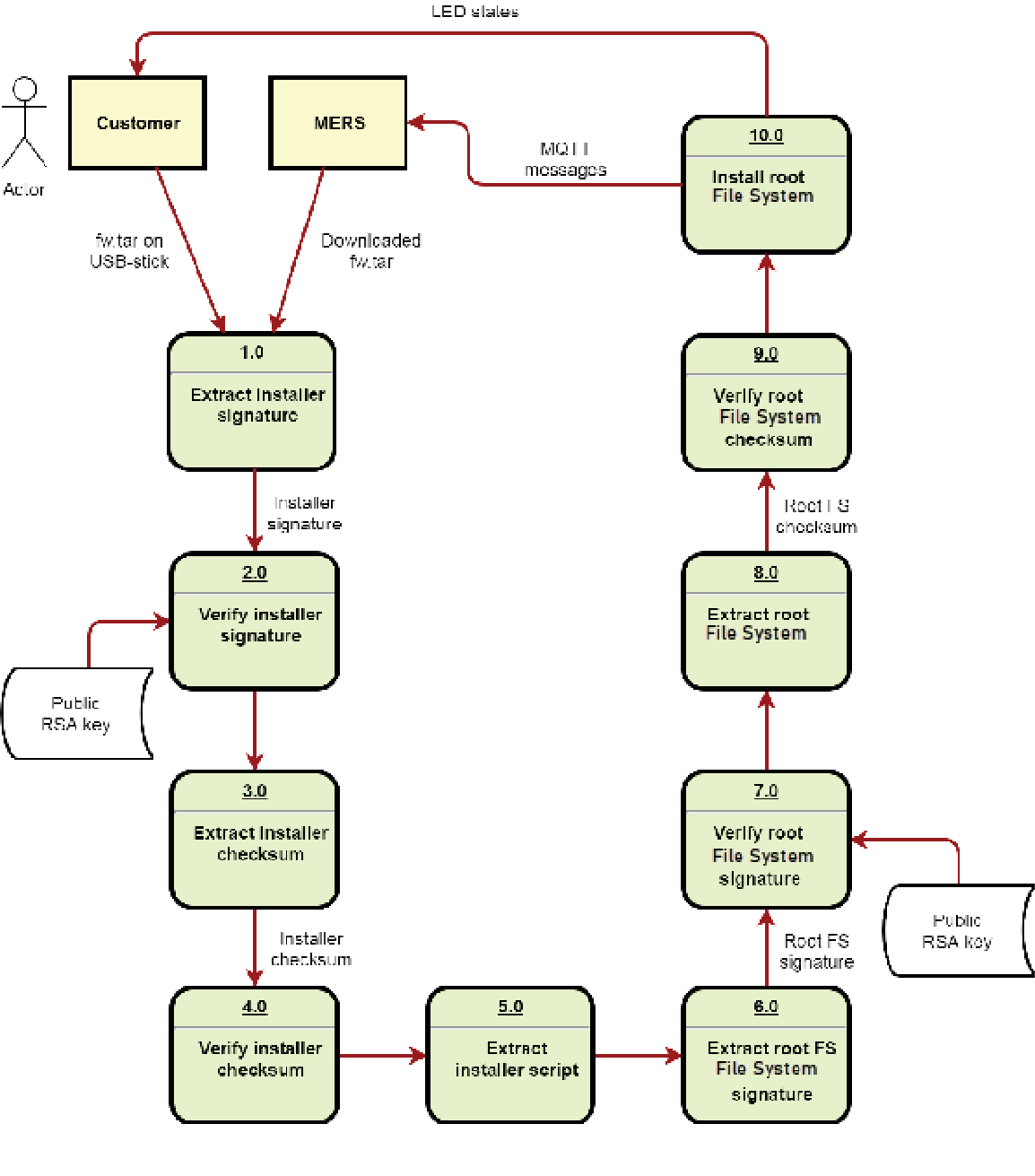
- Before installation, firmware is signed and signature is validated by the device.
Onboarding agent¶
To onboard an agent, establish the trust between agent and agent management:
- Create an agent in Asset Manager.
- Define the network and security profile in Asset Manager.
- Download the initial access token and network configuration to your local machine.
- Deploy the initial access token to agent, for example via USB stick.
With the initial access token, the agent can prove it‘s identity towards agent management by:
- The Initial Access Token (IAT) is physically entitled to onboard the agent.
- The initial access token is valid for 7 days for security measures to avoid the misuse.
Registering an agent¶
To register an agent at agent management, follow the below OAuth 2.0 protocol:
MindConnect Elements uses RSA3072 standard public/private keys in further communication. For example, the agent registers at agent management with the IAT and additionally, a JSON Web-Key is set according to RFC7517 that contains a self generated public key.
Accepting the registration¶
With this response, the agent is onboarded and agent management accepts the registration. There are two cases, the agent management responds with:
Case 1:
- The shared secret (valid for 7 days) – to be used to access token in the request.
- The re-registration access token (RAT) – to be used for the renewal of registration, once the registration is expired.
Case 2:
- The re-registration access token (RAT) – to be used for the renewal of registration, once the registration is expired.
- The agent management stores the public key received after registering an agent and uses it to verify the request access token from agent, which uses JWT signed with private key from now on. For more information, see Onboarding an Agent.
Validity of the credentials¶
By default, each registered agent (either RSA 3072 or Shared Secret security profile) has its own credentials valid for 7 days and it must be renewed on a regular basis. After this period, Insights Hub will not grant any access tokens to the agent and the agent credentials will be invalid. The agent needs to re-register to Insights Hub by providing its Registration Access Token (RAT).
Registration access tokens have no practical expiration times but each time a client refreshes its registration a new RAT is generated by Insights Hub.
API communication agent¶
Except the one for onboarding and registration, all Industrial IoT APIs require an access token:
The Agent requests an access token from Agent IAM using a self signed JSON Web Token (JWT). The JWT is signed (see RFC-7515) with either the shared secret (Case 1) or the private key of the public / private key pair (Case 2) in Step 2. The JWT contains the tenantId
The granted access token is valid for 30 minutes. It is also a JWT and contains:
- tenantId
- scopes: It describes the type of services used in this token holder.
After expiry, a new token needs to be requested.
Firmware management¶
Firmware management is stored in secure cloud storage. Agent accesses secure storage through a signed URL issued by Insights Hub and it is valid for 7 days.
Firmware is signed with private key from Insights Hub. Firmware installer (MERS) on device, checks signature against matching public key provided at initial installation in the factory.