Working with Cross Account Accesses¶
Note
This section is applicable only for region Europe 1.
You need this method for a continuous access to the desired folder for upload. Consider an example where you have an AWS account, where any application resides and this application needs to continuously access IDL folder. In such scenarios, Cross Account Access is useful.
Using cross account access, add one condition while uploading the file in the header which gives full control to bucket owner. If this header is not included in the request, then the request fails with "Access Denied" error.
Header details: "s3:x-amz-acl": "bucket-owner-full-control"
Info
Command to add Header From aws console there is no option to provide this additional request parameter however it can be sent via cli or sdk mode. Below screenshot shows how to use it via cli. 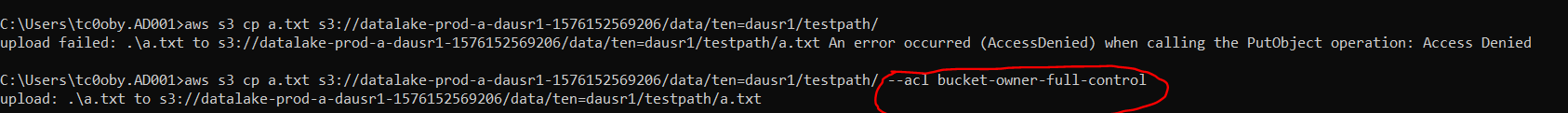
To use this method, you can follow below steps:
-
To create cross account on which access needs to be provided, use the following endpoint:
POST /crossAccountsContent-Type: application/jsonRequest example:
{ "name": "testCrossAccount", "accessorAccountId": "960568630345", "description": "Cross Account Access for Testing", "subtenantId": "204a896c-a23a-11e9-a2a3-2a2ae2dbcce4" }Response example:
{ "id": "0234sd34a23a-11e9-a2a3-2a2sdfw34ce4", "name": "testCrossAccount", "accessorAccountId": "960768132345", "description": "Cross Account Access for Testing", "timestamp": "2019-09-06T21:23:32.000Z", "subtenantId": "204a896c-a23a-11e9-a2a3-2a2ae2dbcce4", "eTag": 1 } -
To get the list of Cross Accounts, use the following endpoint:
GET /crossAccountsContent-Type: application/jsonResponse example:
{ "crossAccounts": [ { "id": "0234sd34a23a-11e9-a2a3-2a2sdfw34ce4", "name": "testCrossAccount", "accessorAccountId": "960768132345", "description": "Cross Account Access for Testing", "timestamp": "2019-09-06T21:23:32.000Z", "subtenantId": "204a896c-a23a-11e9-a2a3-2a2ae2dbcce4", "eTag": 1 } ], "page": { "size": 1, "totalElements": 1, "totalPages": 1, "number": 1 } } -
To get the details of the selected cross account, use the following endpoint:
GET /crossAccounts/0234sd34a23a-11e9-a2a3-2a2sdfw34ce4Content-Type: application/jsonResponse example:
{ "id": "0234sd34a23a-11e9-a2a3-2a2sdfw34ce4", "name": "testCrossAccount", "accessorAccountId": "960768132345", "description": "Cross Account Access for Testing", "timestamp": "2019-09-06T21:23:32.000Z", "subtenantId": "204a896c-a23a-11e9-a2a3-2a2ae2dbcce4", "eTag": 1 } -
To update the selected cross account, use the following endpoint:
PATCH /crossAccounts/0234sd34a23a-11e9-a2a3-2a2sdfw34ce4Content-Type: application/jsonRequest example:
{ "name": "updatedTestCrossAccount", "description": "Updated Cross Account Access for Testing", }Response example:
{ "id": "0234sd34a23a-11e9-a2a3-2a2sdfw34ce4", "name": "updatedTestCrossAccount", "accessorAccountId": "960768132345", "description": "Updated Cross Account Access for Testing", "timestamp": "2019-09-06T21:25:32.000Z", "subtenantId": "204a896c-a23a-11e9-a2a3-2a2ae2dbcce4", "eTag": 1 } -
To delete the selected cross account, use the following endpoint:
DELETE /crossAccounts/0234sd34a23a-11e9-a2a3-2a2sdfw34ce4Response example:
204 Deleted -
Once the cross account is created, create cross account accesses to provide the desired access on desired prefix. This can be done by using teh following endpoint:
POST /crossAccounts/20234sd34a23a-11e9-a2a3-2a2sdfw34ce4/accessesContent-Type: application/jsonRequest example:
{ "description": "Access to read to mysubfolder", "path": "myfolder/mysubfolder", "permission": "READ" }Response example:
{ "id": "781c8b90-c7b6-4b1c-993c-b51a00b35be2", "description": "Access to read to mysubfolder", "storageAccount": "dlbucketname", "storagePath": "data/ten=tenantname/myfolder/mysubfolder", "path": "myfolder/mysubfolder", "permission": "READ", "status": "ENABLED", "timestamp": "2019-11-04T19:19:25.866Z", "eTag": 1 } -
To get details of the cross account accesses, use the following endpoint:
GET /crossAccounts/20234sd34a23a-11e9-a2a3-2a2sdfw34ce4/accessesContent-Type: application/jsonResponse example:
{ "crossAccountAccesses": [ { "id": "781c8b90-c7b6-4b1c-993c-b51a00b35be2", "description": "Access to read to mysubfolder", "storageAccount": "dlbucketname", "storagePath": "data/ten=tenantname/myfolder/mysubfolder", "path": "myfolder/mysubfolder", "permission": "READ", "status": "ENABLED", "timestamp": "2019-11-04T19:19:25.866Z", "eTag": 1 } ], "page": { "size": 1, "totalElements": 1, "totalPages": 1, "number": 1 } } -
To get details of the selected cross account accesses, use the following endpoint:
GET /crossAccounts/20234sd34a23a-11e9-a2a3-2a2sdfw34ce4/accesses/781c8b90-c7b6-4b1c-993c-b51a00b35be2Content-Type: application/jsonResponse example:
{ "id": "781c8b90-c7b6-4b1c-993c-b51a00b35be2", "description": "Access to read to mysubfolder", "storageAccount": "dlbucketname", "storagePath": "data/ten=tenantname/myfolder/mysubfolder", "path": "myfolder/mysubfolder", "permission": "READ", "status": "ENABLED", "timestamp": "2019-11-04T19:19:25.866Z", "eTag": 1 } -
To update the created cross account access, use the following endpoint:
PATCH /crossAccounts/20234sd34a23a-11e9-a2a3-2a2sdfw34ce4/accesses/781c8b90-c7b6-4b1c-993c-b51a00b35be2Content-Type: application/jsonRequest example:
{ "description": "Access to read to mysubfolder", "status": "ENABLED" }Response example:
{ "id": "781c8b90-c7b6-4b1c-993c-b51a00b35be2", "description": "Access to read to mysubfolder", "storageAccount": "dlbucketname", "storagePath": "data/ten=tenantname/myfolder/mysubfolder", "path": "myfolder/mysubfolder", "permission": "READ", "status": "ENABLED", "timestamp": "2019-11-04T19:19:25.866Z", "eTag": 1 } -
To delete the created cross account access, use the following endpoint:
DELETE /crossAccounts/20234sd34a23a-11e9-a2a3-2a2sdfw34ce4/accesses/781c8b90-c7b6-4b1c-993c-b51a00b35be2Response example:
204 deleted -
Once the accesses is provided, you can upload data through CLI or using AWS SDK to the desired prefix with the relevant accesses.
Follow these commands to upload the files to S3 bucket:
$ aws s3 cp myobject.objext s3://tgsbucket
upload: ./myobject.objext to s3://tgsbucket/myobject.objext
Follow these commands to download the files from S3 bucket:
$ aws s3 cp s3://tgsbucket/myobject.objext .
download: s3://tgsbucket/myobject.objext to ./myobject.objext
Except where otherwise noted, content on this site is licensed under the Development License Agreement.